...
- To establish a baseline, the following is proposed:
EVE device is on-boarded in a trusted environment, usually in a manufacturing/supply chain setup (or Intel SDO) - When EVE is on-boarded for the first time, during device-certificate registration, the PCR values coming out of the EVE node will be taken as the baseline for that device. Any change in the PCR value (other than during an EVC-driven upgrade, explained below) after will be flagged as UUD, and unless the user marks it as legal/accepted, the EVE node will remain in the UUD state.
- If the enterprise account is a manufacturing account, then geo-location will be exempted in calculating the baseline.
- When the EVE node comes online for the first time in a non-manufacturing enterprise, geo-location of the EVE node will be taken and will be frozen as the baseline value for geo-location . In case of mobile gateways, there will be an option to turn-off Geo-Fencing(i.e. Locking of Geo location(only if Location-Lock feature is enabled)
Updated EVE Startup State Transition
...
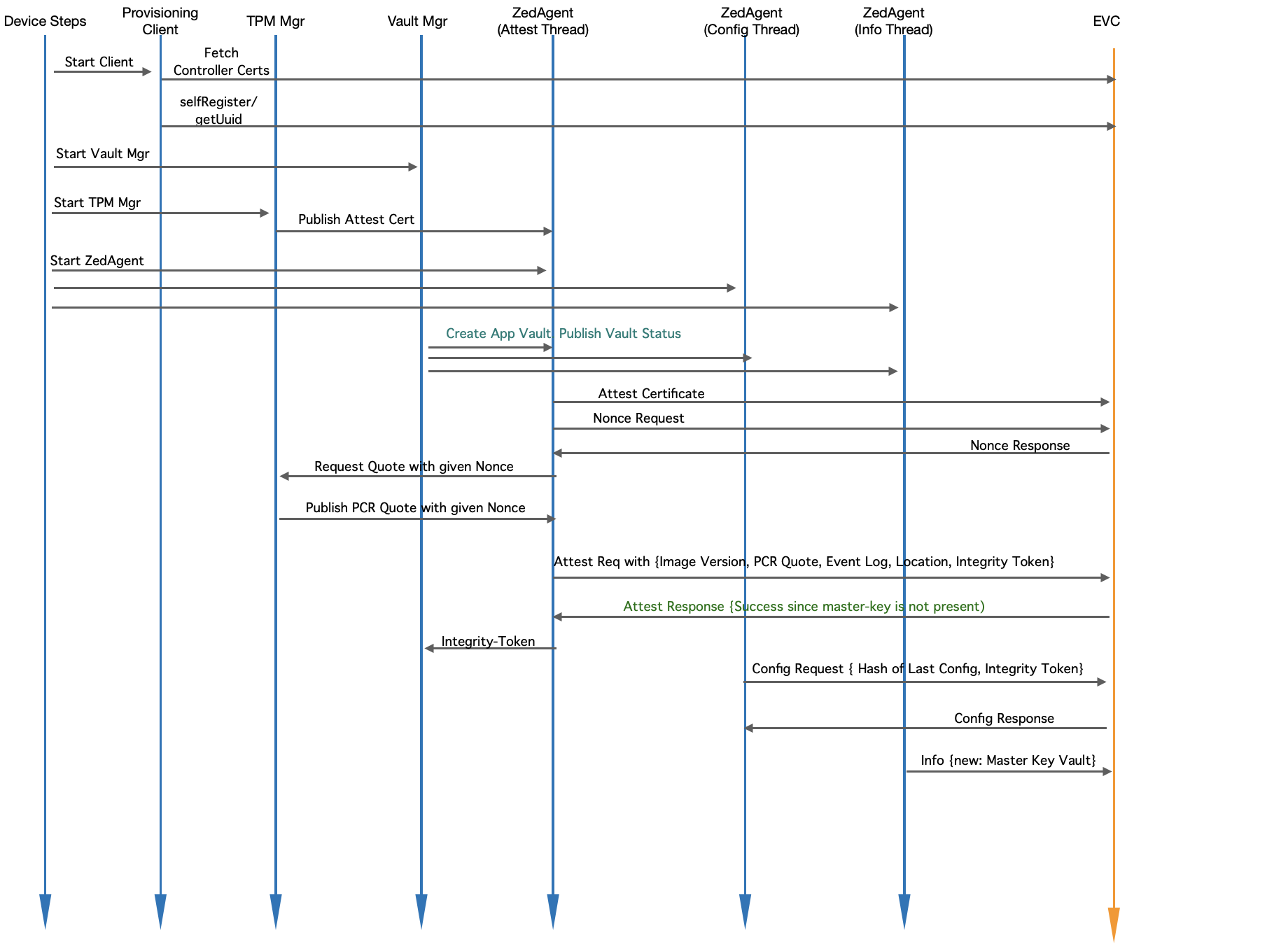
Fig. Module Level Interaction in EVE - Startup Sequence (Post Onboarding)
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- If certificates from EVC are not yet fetched, fetches them
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr retrieves the master decryption key from TPM with Unseal operation
- Unlocks /persist/vault with the master-key
- Publishes vault status (unlocked)
- Waits for Integrity-Token and/or master-key from EVC.
- Once received, rotates the master-key if requested, and also copies the new Integrity-Token to /persist/vault/itoken file
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task picks up the attestation certificate and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, if quote is the same as previous quote, approves the attestation request
- If Location-Lock is enabled, location is checked in addition to Quote
- Along with attestation approval, the encrypted master-key is sent back to EVE
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through)
- Attest task, once attestation request is approved, gets the master-key and Integrity-Token and passes it to Vault Mgr
- Config task now picks up the right Integrity-Token and Config request is now accepted by EVC, and full configuration is sent back
- Info task reports the encrypted master-key back to EVC, for backup purposes
Module Level Interaction - EVE Startup Sequence (Initial Onboarding)
Fig. Module Level Interaction in EVE - Startup Sequence (Onboarding)
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- First fetches EVC Certificates
- Registers the device certificate
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr creates new vault: /persist/vault
- Seals the master-key into TPM with PCR values
- Publishes vault status (unlocked)
- Waits for Integrity-Token from zedAgent
- Once received, rotates the master-key if requested, and also copies the new Integrity-Token to /persist/vault/itoken file
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task picks up the attestation certificate and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, if quote is the same as previous quotemaster-key is not found for the EVE, approves the attestation requestPCR quote as the baseline
- If Location-Lock is enabled, location is checked in addition to Quote
- also approved as baseline (provided the EVE device is not in manufacturing account)
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through)
- Attest task, once attestation request is approved, gets the master-key and Integrity-Token and passes it to Vault Mgr
- Config task now picks up the right Integrity-Token and Config request is now accepted by EVC, and full configuration is sent back
- Info task reports the encrypted master-key back to EVC, for backup purposes
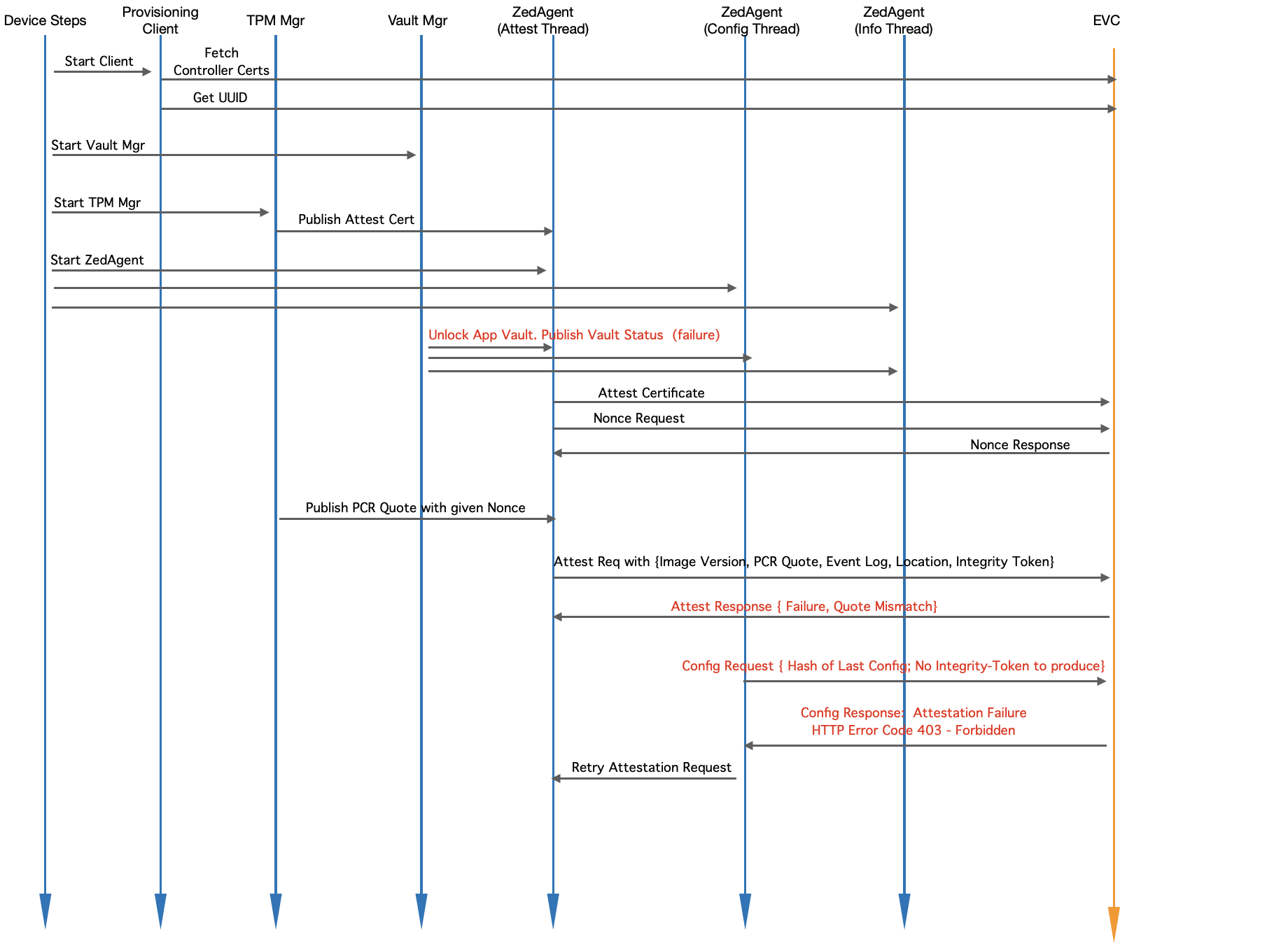
Module Level Interaction - EVE Startup Sequence (Running an Unknown Software)
Fig. Module Level Interaction in EVE - Startup Sequence (Running Unknown Software)Device-steps starts client.go (the provisioning client) which will check and do the following:
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- If certificates from EVC are not yet fetched, fetches them
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr tries to retrieve the master decryption key from TPM with Unseal operation, and Unseal operation fails since the PCR values have changed
- Publishes vault status (as "locked")
- Waits for Integrity-Token and/or master-key from EVC - it will block here forever
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task picks up the attestation certificate and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, since the quote is different, tries to compare EventLog entries with its known hashes against the version reported. Since this is some arbitrary software, there will not be a match.
- Even if Location-Lock is enabled, location can not be trusted here, since the software reporting the location is not trusted.
- EVC sends an error back to EVE, to retry attestation.
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through).
- EVC replies to configuration request, sends partial configuration (only BaseOS upgrade config is sent), and indicates attestation failure (due to no or invalid Integrity Token)
- Config task communicates to Attest Task to re-trigger attestation
Securely Upgrading EVE Software
When EVE goes through a software upgrade, the PCR values might change depending on what is new in the upgraded version. However, during the upgrade window, an attacker might boot a different software as well, and try to present the compromised software as the upgraded version of EVE. Therefore, it is important that we measure the boot sequence after the upgrade and validate that the new software is indeed the new image that was pushed by the EVC. This is done through the following steps:
...