...
Module Level Interaction - EVE Startup Sequence (Running an Unknown Software)
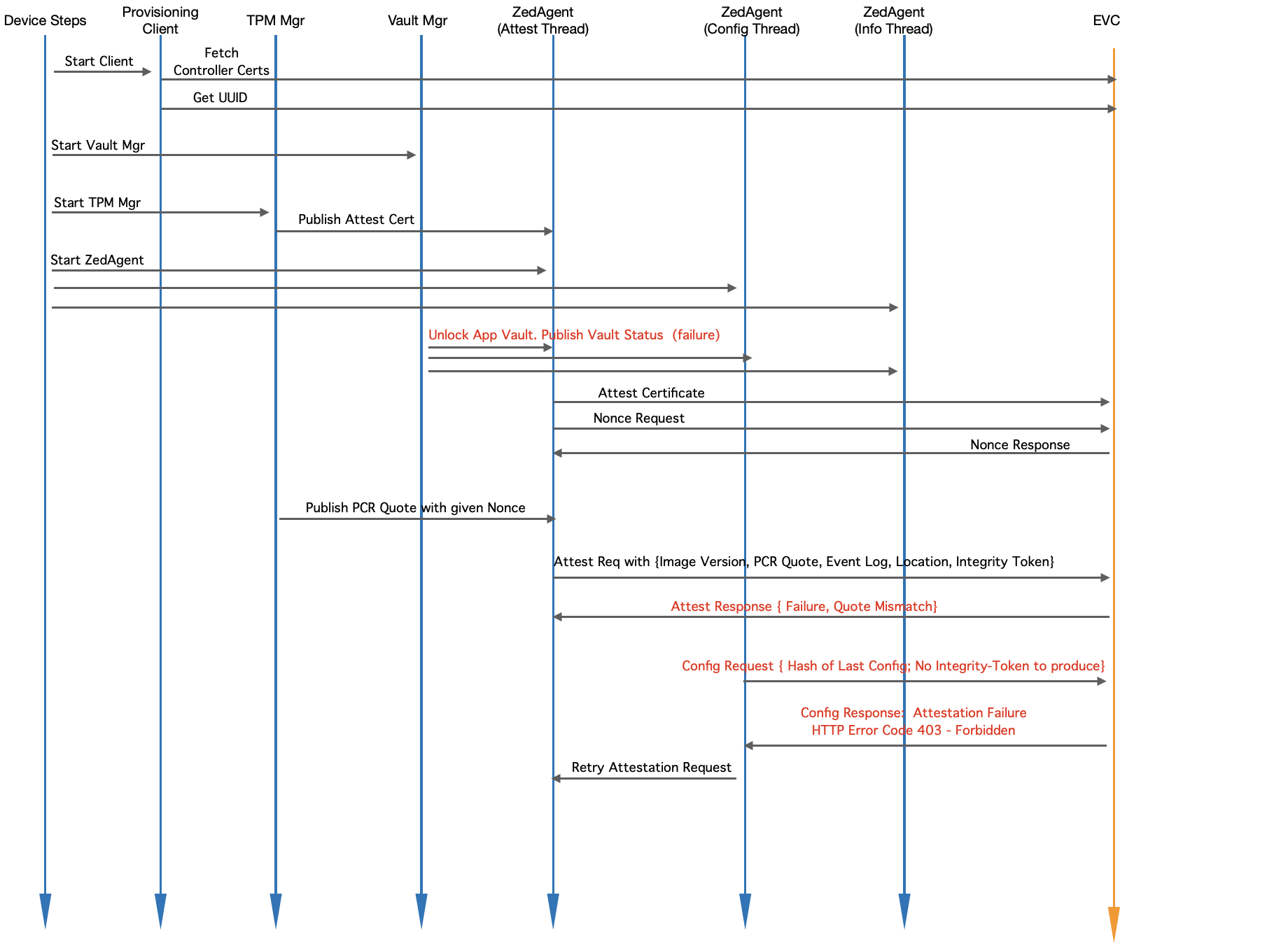
Fig. Module Level Interaction in EVE - Startup Sequence (Running Unknown Software)Device-steps starts client.go (the provisioning client) which will check and do the following:
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- If certificates from EVC are not yet fetched, fetches them
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr tries to retrieve the master decryption key from TPM with Unseal operation, and Unseal operation fails since the PCR values have changed
- Publishes vault status (as "locked")
- Waits for Integrity-Token and/or master-key from EVC - it will block here forever
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task picks up the attestation certificate and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, since the quote is different, tries to compare EventLog entries with its known hashes against the version reported. Since this is some arbitrary software, there will not be a match.
- Even if Location-Lock is enabled, location can not be trusted here, since the software reporting the location is not trusted.
- EVC sends an error back to EVE, to retry attestation.
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through).
- EVC replies to configuration request with HTTP Error Code 403 - Forbidden. Indicates attestation failure (due to no or invalid Integrity Token)
- Config task communicates to Attest Task to re-trigger attestation
...