...
During these extend operations, the extend operations are recorded by BIOS and Bootloader, in a special firmware table, called the TPM Eventlog table, and this table is handed over to the operating system during OS takeover. By playing the same sequence of extend operations recorded in a given TPM Event Log, one can check if the final PCR values match, and if so, then the Event Log(and hence the software layers) can be trusted.
Measuring using PCRs, Verifying using TPM Event Log
Based on the above constructs, we present a solution to measure and attest software integrity of EVE node. Just for recap, EVE is the open-source software from LF-Edge for Edge Virtualization, running on IoT Edge gateways. EVC is the controller for managing these EVE instances. Adam under LF-Edge is an open source implementation of one such EVC. The APIs between EVE and EVC are specified in EVE API specification. In the context of remote attestation, the EVC is the attesting authority and EVE reports its measurements for attestation.
...
Fig 1. Role of EVC as the Remote Attestation Server
Measured Boot vs Secure Boot
Software Layers in EVE Booting Process
Introduction to fundamental constructs used
...
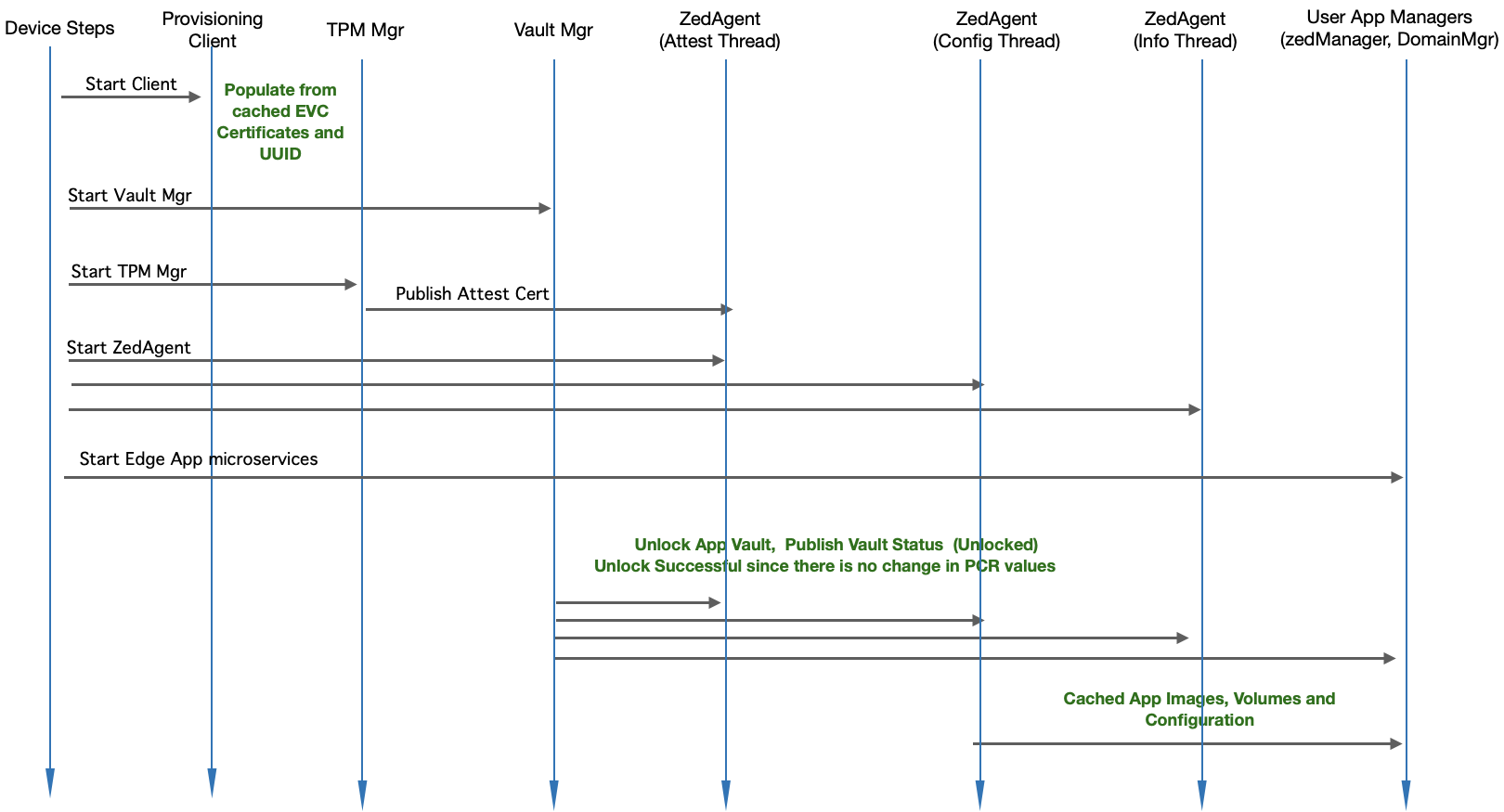
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- First fetches EVC Certificates
- Registers the device certificate
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr creates new vault: /persist/vault
- Seals the master-key into TPM with PCR values
- Publishes vault status (unlocked)
- Waits for Integrity-Token from zedAgent
- Once received, copies the new Integrity-Token to /persist/vault/itoken file
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task,
- picks up the attestation certificate and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once Once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends Sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, if master-key is not found for the EVE, approves the PCR quote as the baseline
- If Location-Lock is enabled, location is also approved as baseline (provided the EVE device is not in manufacturing account)
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through)
- Attest task, once attestation request is approved, gets the master-key and Integrity-Token and passes it to Vault Mgr
- Config task now picks up the right Integrity-Token and Config request is now accepted by EVC, and full configuration is sent back
- Info task reports the encrypted master-key back to EVC, for backup purposes
Module Level Interaction - Startup Sequence (Reboot with no change) - No EVC connectivity required
...
Fig. Module Level Interaction in EVE - Startup Sequence (Post OnboardingReboot with no change; works without EVC connectivity)
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- If EVC is not reachable, uses certificates from the last download
- If EVC are is not yet fetched, fetches them Retrieves UUID from EVCreachable, uses UUID already present in /config/uuid
- Device-steps starts Vault Mgr
- Vault Mgr retrieves the master decryption key from TPM with Unseal operation. Unseal is successful since the PCR values are the same since last reboot.
- Unlocks /persist/vault with the master-key.
- Publishes vault status (unlocked)
- Waits for Integrity-Token and/or master-key from EVC.
- Once received, rotates the master-key if requested, and also copies the new Integrity-Token to /persist/vault/itoken file
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zed Manager, Domain Mgr microservices - these services are responsible for launching the Edge App Instances
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task picks up the attestation certificate Configuration task, since EVC is not reachable, uses the configuration from the last download, and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, if quote is the same as previous quote, approves the attestation request
- If Location-Lock is enabled, location is checked in addition to Quote
- Along with attestation approval, the encrypted master-key is sent back to EVE
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through)
- Attest task, once attestation request is approved, gets the master-key and Integrity-Token and passes it to Vault Mgr
- Config task now picks up the right Integrity-Token and Config request is now accepted by EVC, and full configuration is sent back
- Info task reports the encrypted master-key back to EVC, for backup purposes
Module Level Interaction - EVE Startup Sequence (Reboot with a change)
Fig. Module Level Interaction in EVE - Startup Sequence (Running Unknown Software)
- Zed Mgr and Domain Mgr
- Since the Vault is unlocked, Domain Mgr can access Edge App Images, and hence launches the app instances.
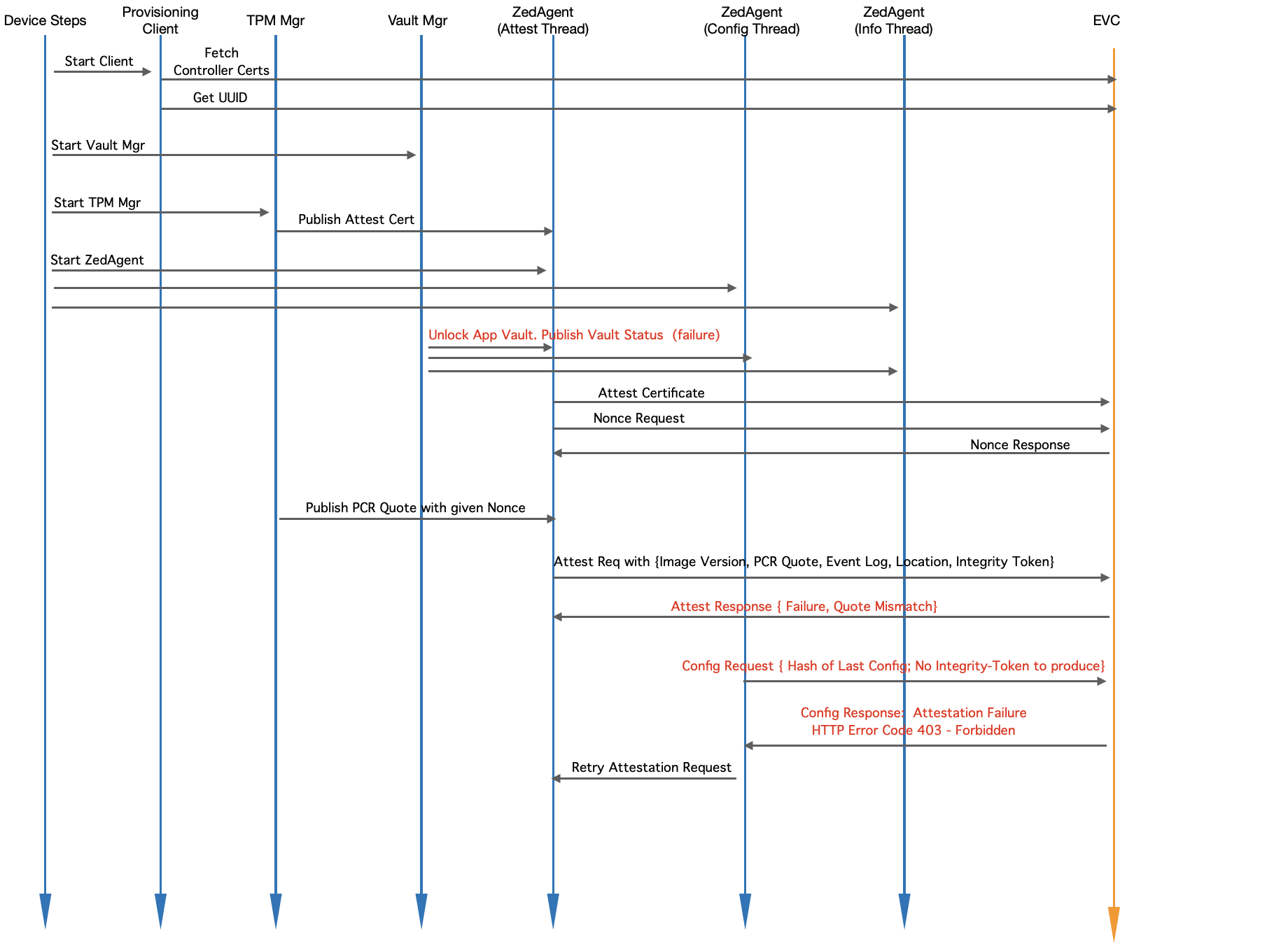
Module Level Interaction - EVE Startup Sequence (Reboot with a change)
Fig. Module Level Interaction in EVE - Startup Sequence (Reboot with differing PCR values)
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- If certificates from EVC are not yet fetched, fetches them
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr tries to retrieve the master decryption key from TPM with Unseal operation, and Unseal operation fails since the PCR values have changed
- Publishes vault status (as "locked")
- Waits for Integrity-Token and/or master-key from EVC - it will block here forever
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Device-steps starts Edge App microservices - e.g. Domain Mgr
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, since the quote is different, tries to compare EventLog entries with its known hashes against the version reported. Since the PCR values are different, there will not be match, unless Admin has uploaded measurements for this new version. Assuming that Admin is yet to upload, attestation request will fail here.
- EVC sends an error back to EVE, to retry attestation.
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through).
- EVC replies to configuration request with HTTP Error Code 403 - Forbidden. Indicates attestation failure (due to no or invalid Integrity Token)
- Config task communicates to Attest Task to re-trigger attestation
- Admin uploads measurements for the new image version
- The next attestation request is matched successfully against the uploaded measurements
- EVC approves the attestation request, and responds back with the master-key (encrypted with TPM key) for the EVE node, and also saves the Integrity-Token supplied in the attestation request
- Vault Mgr
- picks up the master-key
- unlocks vault
- populates Integrity-Token approved by EVC inside /persist/vault/itoken
- Publishes new vault status (unlocked) to all the microservices
- The next configuration request picks up the new Integrity Token, and sends configuration request along with this Integrity-Token
- EVC verifies that Integrity-Token matches with its copy, and approves configuration request and responds with the latest configuration.
- Domain Mgr notices the new vault status (unlocked) from Vault Mgr , and latest configuration from ZedAgent, and starts the Edge Apps
- Info task reports the encrypted master-key back to EVC, for backup purposes
- Device-steps starts client.go (the provisioning client) which will check and do the following:
- If certificates from EVC are not yet fetched, fetches them
- Retrieves UUID from EVC
- Device-steps starts Vault Mgr
- Vault Mgr tries to retrieve the master decryption key from TPM with Unseal operation, and Unseal operation fails since the PCR values have changed
- Publishes vault status (as "locked")
- Waits for Integrity-Token and/or master-key from EVC - it will block here forever
- Device-steps starts TPM mgr
- TPM manger retrieves the attestation certificate and publishes to Zedagent
- Waits for Quote requests on pubsub channel from Zedagent
- Device-steps starts Zedagent (and Zedagent starts 3 concurrent tasks: attest, info and config)
- Attest task picks up the attestation certificate and publishes to EVC
- Attest task requests for a nonce from EVC (to prepare PCR quote)
- Attest task sends the nonce back to TPM Mgr and waits for PCR quote
- Attest task, once notified about the quote readiness, creates a random nonce value for Integrity-Token
- Attest task sends { Quote, Location, Event Log, Integrity-Token, Image Version } to EVC
- EVC, since the quote is different, tries to compare EventLog entries with its known hashes against the version reported. Since this is some arbitrary software, there will not be a match.
- Even if Location-Lock is enabled, location can not be trusted here, since the software reporting the location is not trusted.
- EVC sends an error back to EVE, to retry attestation.
- In the mean time, configuration task keeps requesting config from EVC (expected to fail till attestation goes through).
- EVC replies to configuration request with HTTP Error Code 403 - Forbidden. Indicates attestation failure (due to no or invalid Integrity Token) Config task communicates to Attest Task to re-trigger attestation
Securely Upgrading EVE Software
...
Fig 4. Firmware Upgrade Management