...
Please note: There are some measured boot solutions which behave more like secure boot, there are some secure boot solutions which behave more like measured boot, but the reader is advised to stick to the above definitions, for the purpose of discussions in this document.
| Secure Boot | Measured Boot |
|---|---|
| Core Root of Trust is certificate embedded in Firmware by OEM | Core Root of Trust is Trusted Platform Module (TPM) |
| Does not require connectivity to any remote verifier to establish chain of trust. | verifier needs to inspect TPM PCR values before booting process can be trusted |
| Any new software needs to be signed by a certificate rooted to OEM certificates | An independent trusted third-party (an verifier), can match the PCR measurements against its expected values |
| Chain of trust is established by each software layer verifying the next software layer before handing the control over (in the boot chain) | Chain of trust is established after going through TPM Event Log and PCR values |
| Device will become inaccessible if one of the software layers fail validation since booting process will halt. Good for devices with human presence like smartphones, laptops etc. But poses difficulty for remotely managed systems like IoT Edge gateways, where manual access to the device is limited. Since IoT gateways are managed through remotely located controllers, losing connectivity will severely impact visibility into the system. | Works well for remotely managed systems. Device will be accessible, and controller can still reach the system, and get visibility into the system. |
As you can see, both the standards have their own merits and demerits when considering security requirements for a remotely managed EVE system. i.e.
...
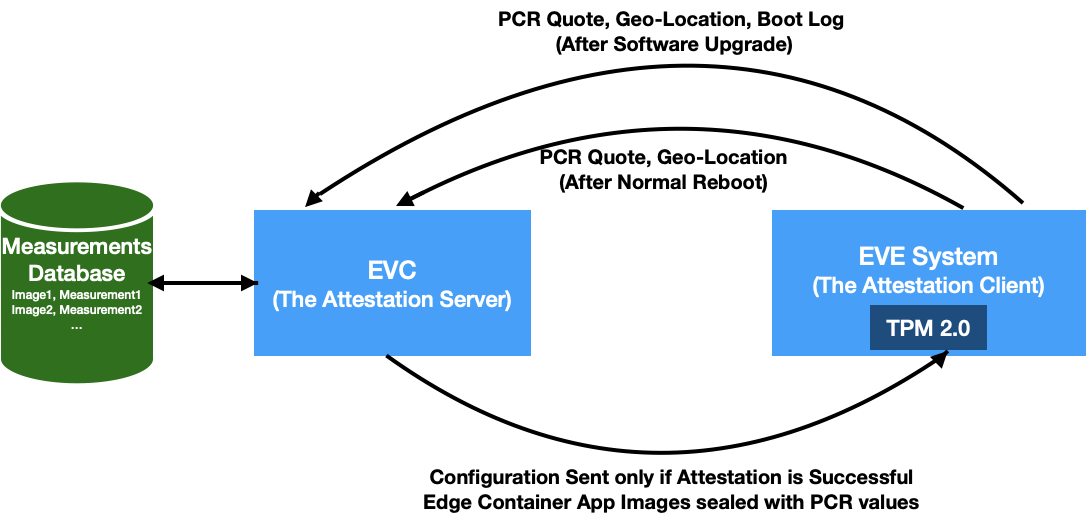
Based on the above constructs, we present a solution to measure and attest software integrity of EVE node. Just for recap, EVE is the open-source software from LF-Edge for Edge Virtualization, running on IoT Edge gateways. EVC is the controller for managing these EVE instances. Adam under LF-Edge is an open source implementation of one such EVC. The APIs between EVE and EVC are specified in EVE API specification. In the context of remote attestation, the EVC is the attesting authority and EVE reports its measurements for attestation.
Fig 1. Role of EVC as the verifier, and EVE as the attester
...