Problem Statement
- Currently sensitive configuration blocks for an EVE-node, not all-inclusive, are data store credentials, WLAN credentials, cloud-init (containing Azure/AWS credentials) etc.
- EVE controller posts these sensitive configuration, in clear-text format, as part of the configuration blob to EVE node. The sensitive configuration blocks are exchanged between agents inside the EVE node, as is through pubsub channel.
Motivation
As part of data at rest/transition encryption initiative, for EVE, the sensitive configuration block should be in encrypted format during the transit from EVE controller and EVE node, and while at rest(pubsub channel storage) inside EVE node, until the end-user consumer uses them.
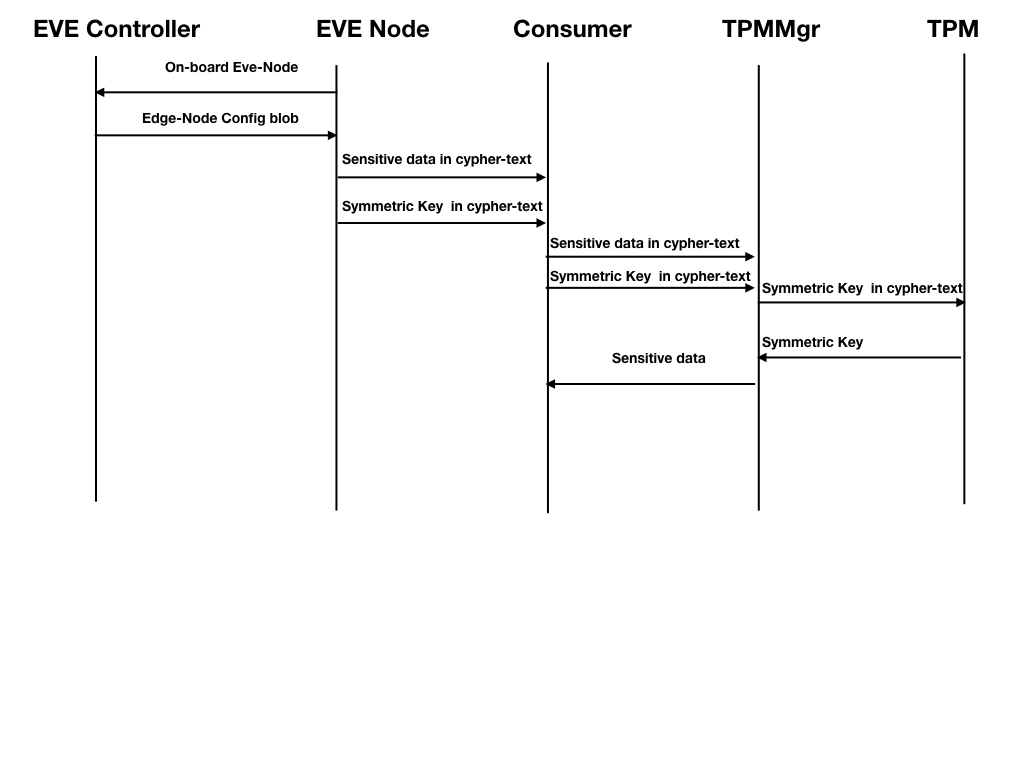
Proposed Solution
- Every sensitive configuration block will contain a set of attributes storing the encryption configuration (symmetric key value in cypher text, key size and encryption algorithm .e.g., "keySize": "256" bits, "algorithm": "AES-256" etc.) that was used to encrypt the configuration block
- EVE Controller will generate a symmetric key for every sensitive configuration block. Alternatively, EVE controller can use the same key for all the sensitive configuration blocks.
- EVE Controller will use symmetric Key(s) to encrypt these above mentioned sensitive configuration blocks, using standard encryption methods ( AES-256 etc.) using standard software crypto tools ( e.g. openssl or, go crypto etc.)
- EVE controller will wrap/seal the symmetric key(s) using device certificate of the EVE node, for each sensitive configuration block, before posting to the EVE-Node.
- These symmetric key(s) generation/rotation can be driven by user defined policies, which is beyond the scope of this document. EVE controller can also generate these symmetric keys, while constructing the configuration blob for an EVE node, and discard them after that, by not storing them inside any database.
- Inside EVE-node, the sensitive configuration stays in encrypted format on disk (i.e., pubsub), and will only be decrypted on demand by the end consumer.
- The end consumer module (e.g. downloader), will unwrap/unseal the symmetric key with the help of TPM-Mgr (using standard go-tpm APIs), and construct the symmetric key first, and then use the symmetric key to decrypt the sensitive configuration block, using software crypto tools (e.g. openssl or go crypto etc.)